Title: Improper Input Validation leads to buffer overflow in dlt-daemon
Date: 12/05/2021
CVE-ID: CVE-2021-29507
Author: Thomas Sermpinis
Versions: 2.10.0 < version <= 2.18.6
Package URL: https://github.com/GENIVI/dlt-daemon/
Tested on: dlt-daemon 2.18.6
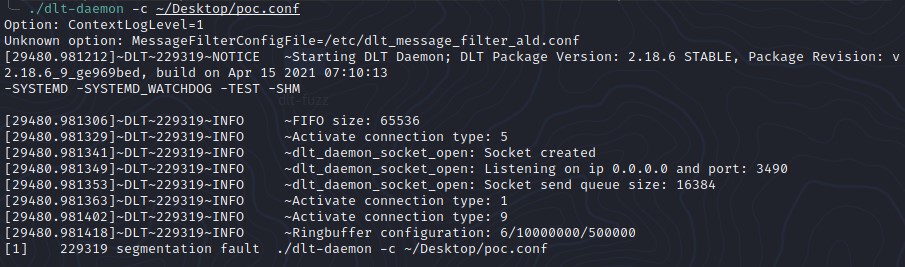
The dlt-daemon includes a configuration file load functionality (-c) which is vulnerable to a buffer overflow vulnerability and allows a malicious user to supply a specially crafted configuration file which results in a segmentation fault after improper validation of the file content.
What kind of vulnerability is it? Who is impacted? The vulnerable component could be crashed when the configuration file is intentionally/unintentionally containing the special characters. All the applications which are using could fail to generate their dlt logs in system.
